Constraining Resource Access To Group Members
The following example demonstrates how you can leverage the combined power of a SPARQL ASK Query and Web-accessible Linked Data en route to constraining access to a protected resource. Basically, you put two resource to use:
- A protected resource accessible from a location on the Web via its URL .
- A read-only resource accessible from a location on the Web that describes a Group and its Membership.
- Prerequisites
- 1. Describe your group and it membership via a Turtle document, for instance (you can user other RDF model syntaxes, but we choose use Turtle for its simplicity)
- 2. Create a Web document comprised of content that describes the group
- 3. Create a Web document that should only be accessible to members of the new group
- 4. Share the Web document URL with group members.
- 5. View the shared document
- Related
Prerequisites
The following packages should be installed, prior to performing this exercise:
1. Describe your group and it membership via a Turtle document, for instance (you can user other RDF model syntaxes, but we choose use Turtle for its simplicity)
- Group Description using terms from the FOAF & RDFS vocabularies :
@prefix rdfs: <http://www.w3.org/2000/01/rdf-schema#> . @prefix foaf: <http://xmlns.com/foaf/0.1/> . @prefix : <#> . <> foaf:topic :Group . <> rdfs:label "Social Semantics & ACLs Demo" . <> rdfs:comment "Members of this group provide the basis for a Resource Access Policy scoped to this group." . :Group a foaf:Group . :Group foaf:member <http://id.myopenlink.net/dataspace/person/kate#this> , <http://id.myopenlink.net/dataspace/person/john#this> .
- The document content above implies that <http://web.ods.openlinksw.com/DAV/home/demo/Public/group.ttl#Groupgt; denotes the Group.
2. Create a Web document comprised of content that describes the group
Publish the Turtle Document to a Web accessible location, using ODS-Briefcase, as follows:
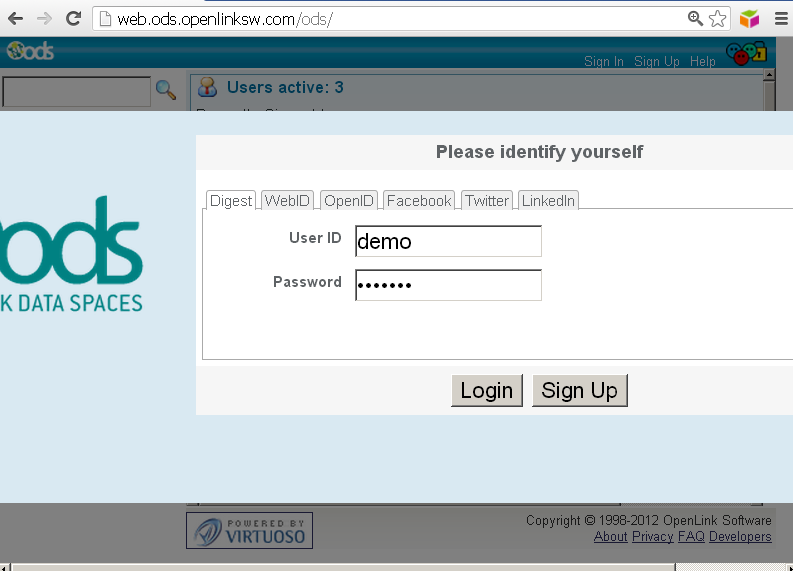
- Log in at http://web.ods.openlinksw.com/ods ->Sign In and enter user's credentials:
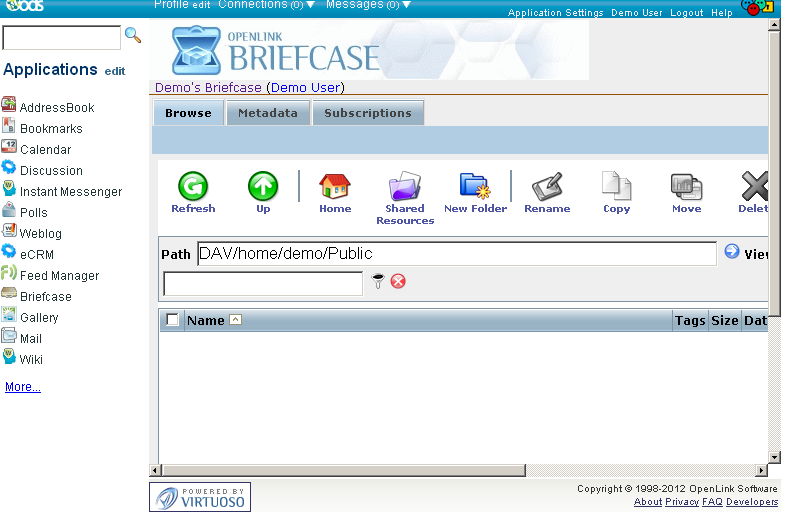
- Go to Briefcase and navigate for to its Public folder:
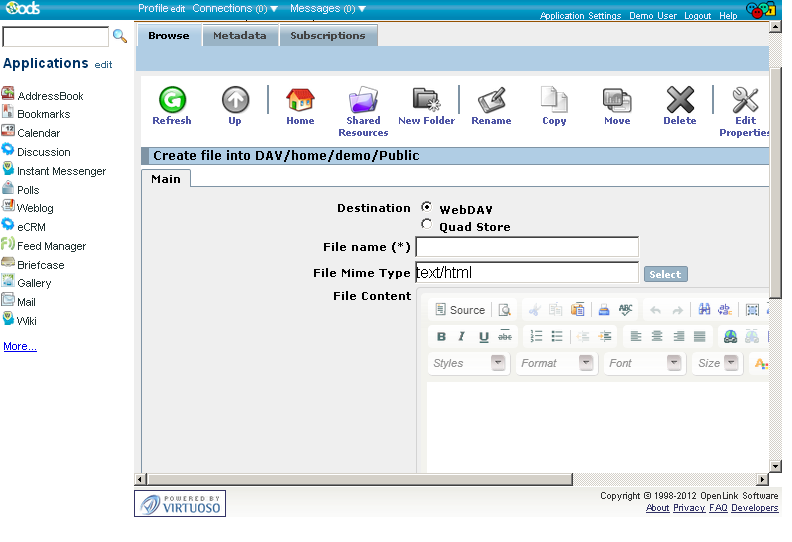
- Click "Create":
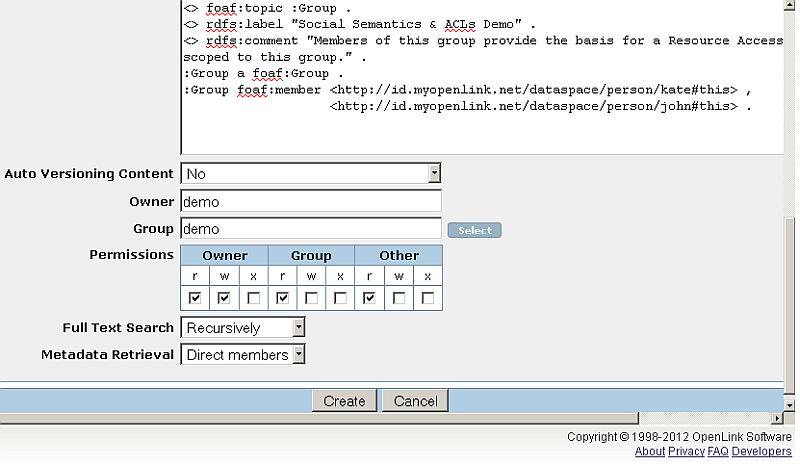
- In the presented form:
- Finally click "Create".
- Your file should be created and displayed Briefcase's folder viewer:
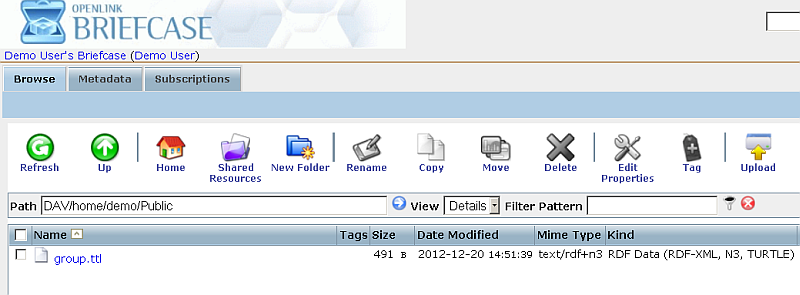
- Note: if you not using the "Public" folder (which provides public access by default), please make sure you set make the document available to the public, i.e.
it should have permissions:
rw-r--r--
- Note: if you not using the "Public" folder (which provides public access by default), please make sure you set make the document available to the public, i.e.
it should have permissions:
3. Create a Web document that should only be accessible to members of the new group
- Assuming you (an ODS account holder named 'William') want to only share the image resource (below) with two people: Kate and John, please perform the following steps:
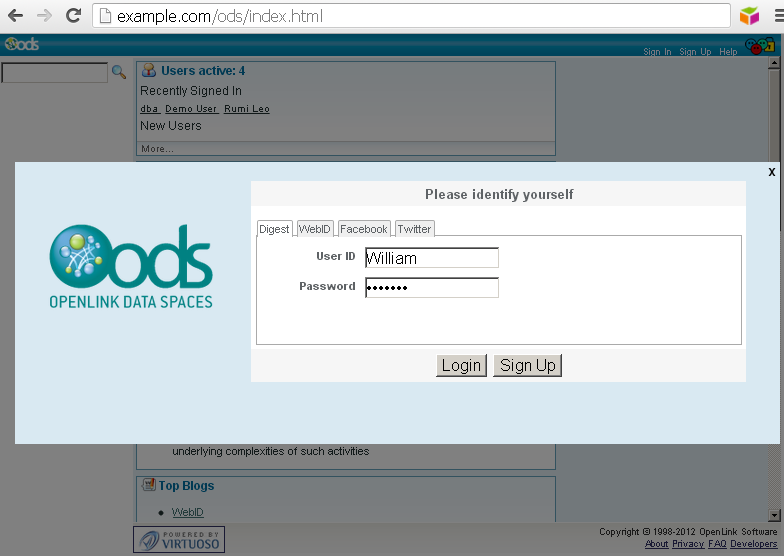
- Go to http://host:port/ods and login with your credentials:
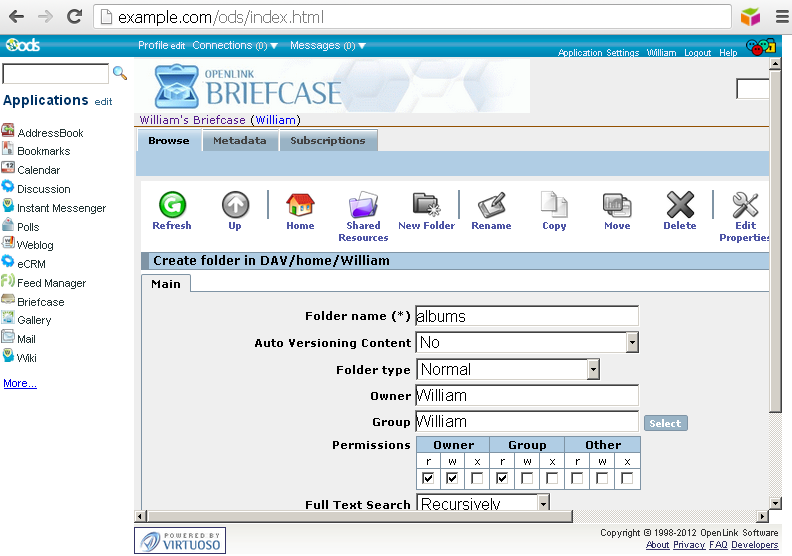
- Click on the Briefcase application link and click on the "New Folder" menu item to create the sub-folder: "albums":
- Click "Create".
- The new created folder should be presented in the list of folders and resources for user William:
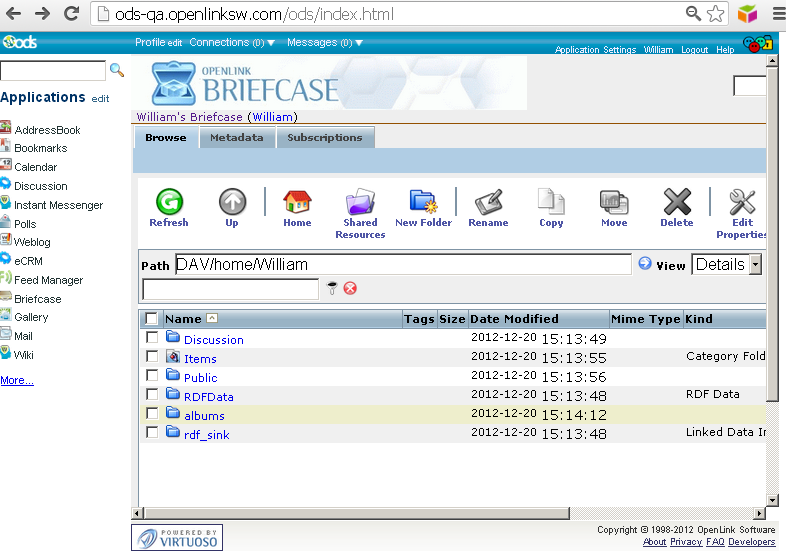
- Go to "albums" folder and using the "Upload" feature upload the image "OpenLink.png" from above:
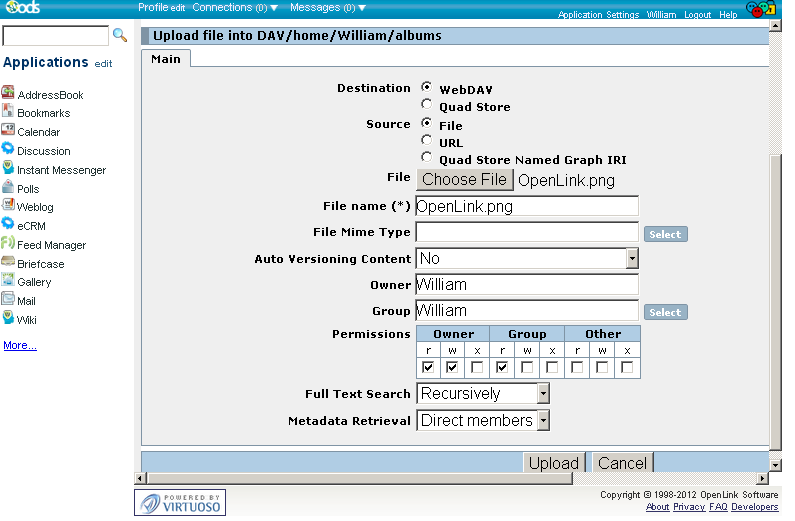

4. Share the Web document URL with group members.
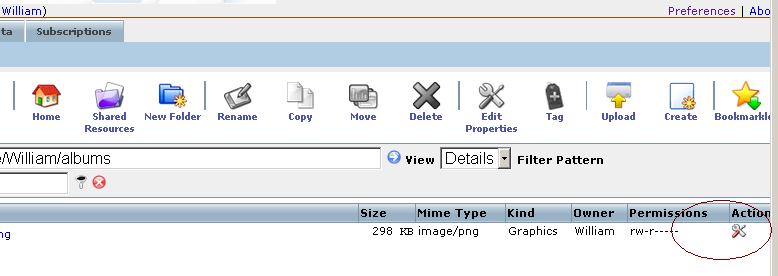
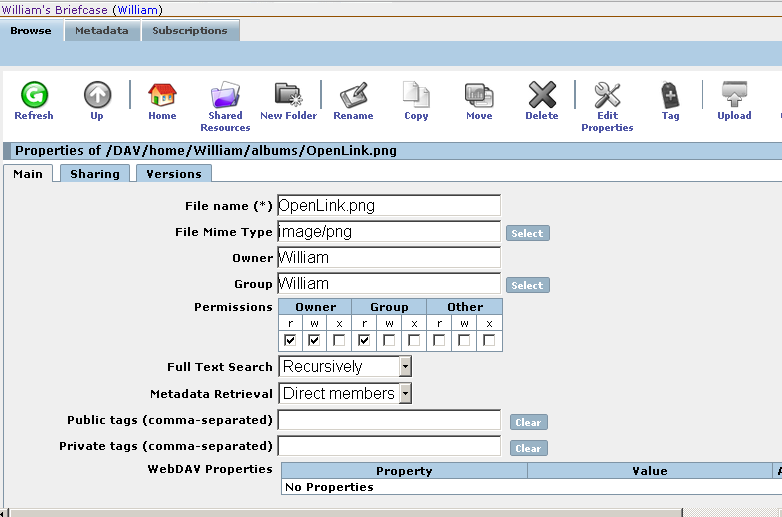
- For the uploaded image "Openlink.png" from above, navigate to the Briefcase UI DAV path containing the image, and click its "Update Properties" link:
- Go to "Sharing":
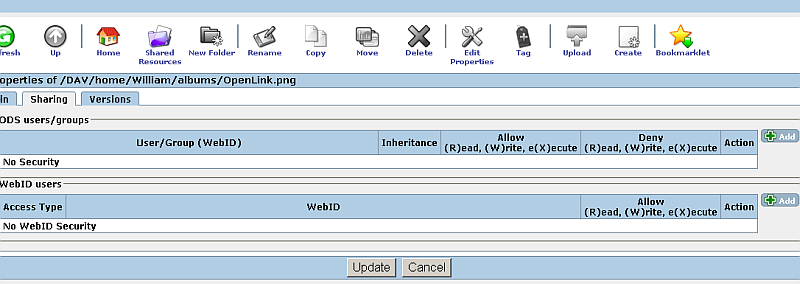
- In "WebID users" section click the green "plus" button with label "Add":
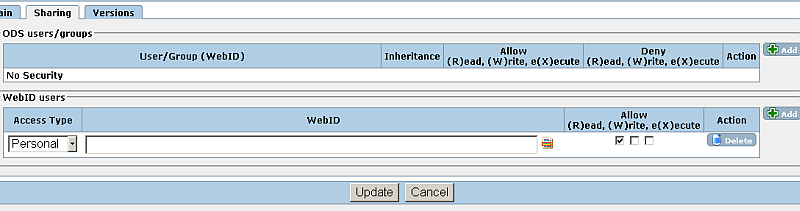
- In the presented form:
- Change "Access type" to "Advanced";
- For "Criteria" click the green "plus" button and select "Certificate - SPARQL ASK"
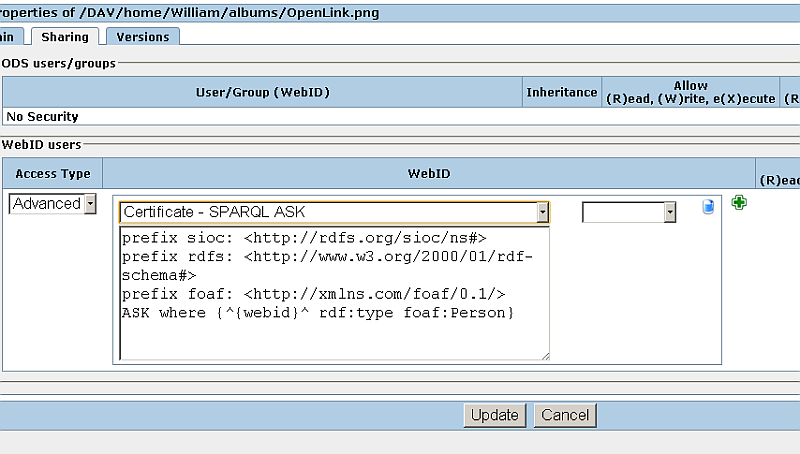
- Should appear a drop-down menu list with 2 values: "equal to" and "not equal to".
Select the "equal to" value:
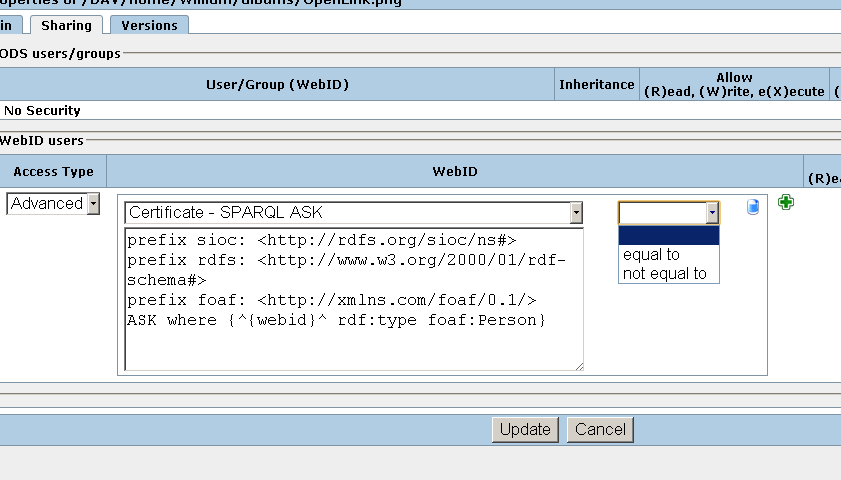
- Should appear a drop-down menu list with 2 values: "yes" and "no".
Leave the default presented value "yes" as selected:
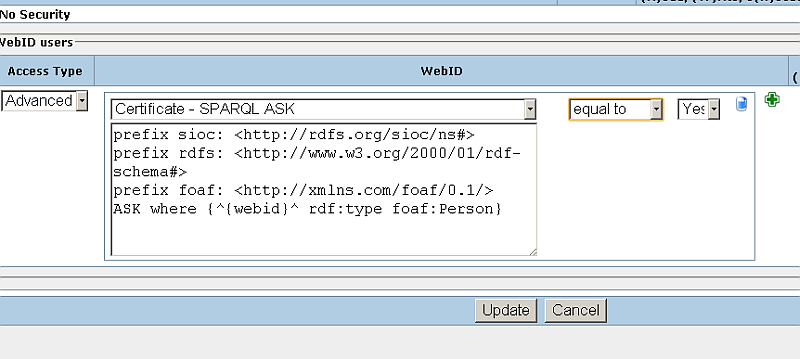
- Modify the SPARQL ASK statement by replacing it with this one:
DEFINE get:soft "replace" PREFIX sioc: <http://rdfs.org/sioc/ns#> PREFIX rdfs: <http://www.w3.org/2000/01/rdf-schema#> PREFIX foaf: <http://xmlns.com/foaf/0.1/> ASK FROM <http://web.ods.openlinksw.com/DAV/home/demo/Public/group.ttl> WHERE {<http://web.ods.openlinksw.com/DAV/home/demo/Public/group.ttl#Group> foaf:member ?x}
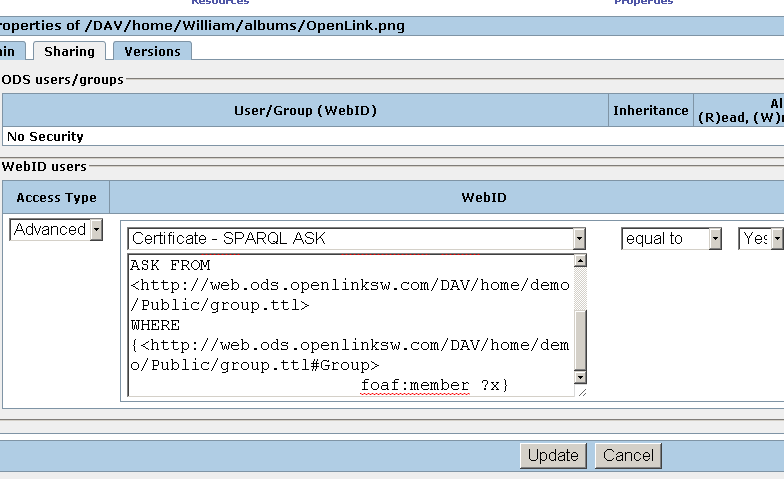
- Click "Update":
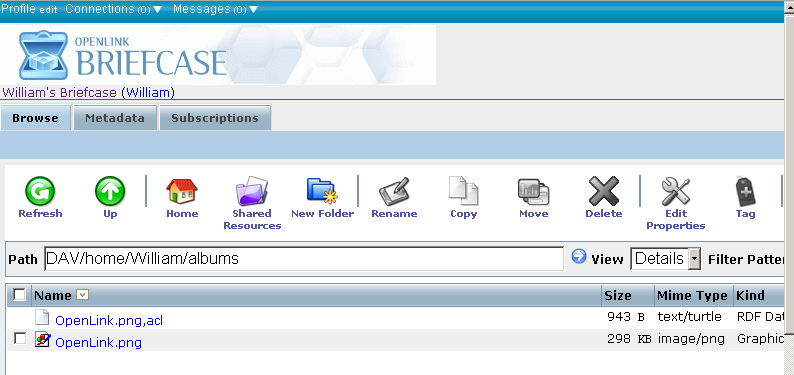
5. View the shared document
- As per the sharing done from above, users Kate and John should be able to see the Web document
https://host-port//DAV/home/William/albums/OpenLink.pngif they authenticate with X 509. Watermarked Certificate containing the WebIDs included in the group.ttl from above. - Navigate to
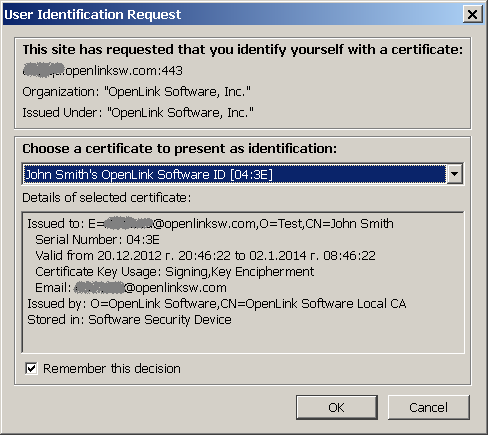
https://host-port//DAV/home/William/albums/OpenLink.png - When prompted for authentication, select for ex.
John's X 509 WebID Watermarked Certificate:
- John should successfully view the shared Web document -- in our example a simple image:
Related
- Confining Resource (Data) Access to a Group Entity
- Power of WebID + OpenID Hybrid Protocol via Internet Explorer & Windows
- Using Safari to Demonstrate WebID + OpenID Hybrid Protocol Power!
- Safeguarding your Virtuoso-hosted SPARQL Endpoint
- SPARQL Endpoint Protection Methods Collection
- Constraining Resource Access Using Social Relationship Semantics and WebID
- Virtuoso documentation
- Virtuoso Tips and Tricks Collection
- SPARUL over SPARQL using the http://cname:port/sparql-auth endpoint
- Virtuoso Authentication Server UI
- Manage a SPARQL-WebID based Endpoint
- WebID Protocol Support in OpenLink Data Spaces.
- Manage ODS Datadspaces Objects WebID Access Control Lists (ACLs):
- Guide for Set up a X.509 certificate issuer and HTTPS listener and generate ODS user certificates
- Configure Virtuoso+ODS instance as an X.509 Certificate Authority and HTTPS listener
- Configure Virtuoso instance as an X.509 Certificate Authority and HTTPS listener
- Setting up PubSubHub in ODS
- PubSubHub Demo Client Example
- Feed subscription via PubSubHub protocol Example
- Setting Up PubSubHub to use WebID Protocol or IP based control lists
- CA Keys Import using Conductor
- Generate an X.509 Certificate (with a WebID watermark) to be managed by host operating system keystore
- Generate an X.509 Certificate (with a WebID watermark) to be managed by a browser-based keystore
- Using Virtuoso's WebID Verification Proxy Service with a WebID-bearing X.509 certificate
- Using Virtuoso's WebID Identity Provider (IdP) Proxy Service with an X.509 certificate
- ODS Briefcase WebID Protocol Share File Guide
- WebID Protocol Specification
- Test WebID Protocol Certificate page
- WebID Protocol Certificate Generation page