How can I use LDAP based WebIDs?
What?
Use of LDAP scheme (ldap:) URIs as bona fide WebIDs that are verifiable using the WebID protocol.
Why?
As a protocol, WebID is about verifying Identity via de-referencable URIs for Agents (people, organizations, programs). Thus, bearing in mind the multi scheme essence of URIs, and the fact that many existing systems already leverage X.500 names as part of LDAP setups, its vital that WebID usage extends naturally to these setups; especially, when introducing WebID to organizations, unobtrusively.
How?
The steps that follow walk you through the process of generating an X.509 Certificate that has an ldap: URI value in the Subject Alternate Name (SAN) and then using this Certificate to verify Identity using the WebID protocol.
Basic steps for setting up LDAP Server, generating and importing certificate with WebID in the LDAP server
- Setup LDAP to Virtuoso instance binding via Conductor UI.
- As LDAP query works based on the attribute=value from profile, perform LDAP lookup test:
- Access the following URL:
https://mail.openlinksw.com/ldapinfo.php?dn=uid=john,ou=Accounts,o=OpenLink%20Software,c=US
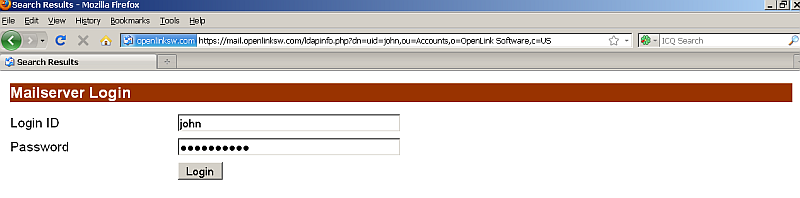
- Post successful authentication should show the user details:
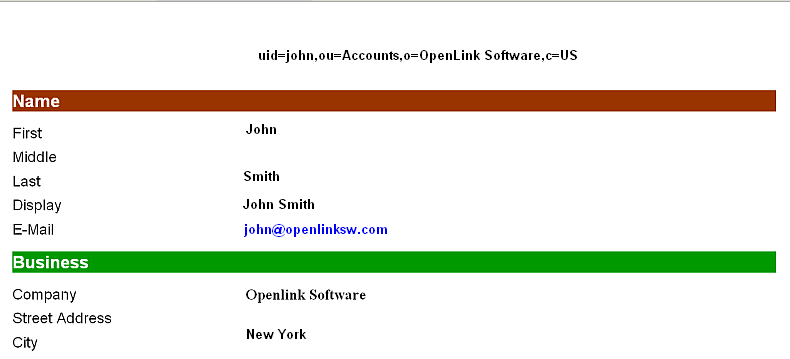
- Access the following URL:
- Set up of an X.509 certificate issuer and HTTPS listener
- Generate certificate with LDAP based WebID via ODS or another method, by placing LDAP: scheme URI in SAN of the Certificate to be generate, for ex:
ldap://mail.openlinksw.com/cn=John%20Smith%2Cou=Accounts%2Co=OpenLink%20Software%2Cc=US
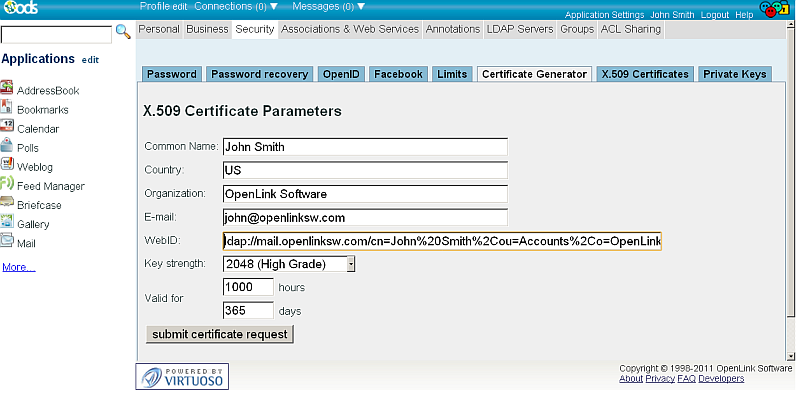
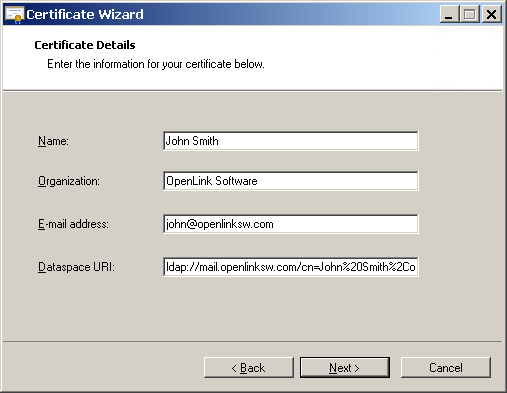
- Convert from p12 to DER format: Suppose the certificate generated from the previous step is exported as p12 format . To convert it to DER format, one should perform the following commands:
openssl pkcs12 -in mykey.p12 -nokeys > mykey.pem openssl x509 -in mykey.pem -outform DER > mykey.crt
- LDAP Setup:
- Start LDAP manager UI e.g. http://mail.openlinksw.com
- Post successful authentication click on Profile
- Update the "Country" and "Company" (Organization) fields if empty
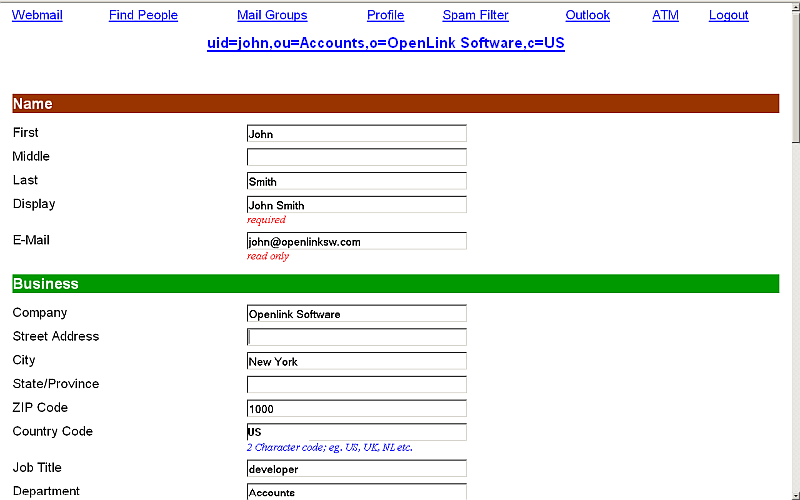
- Go to security section as import X.509 Cert so that DN is now associated with a Public Key.
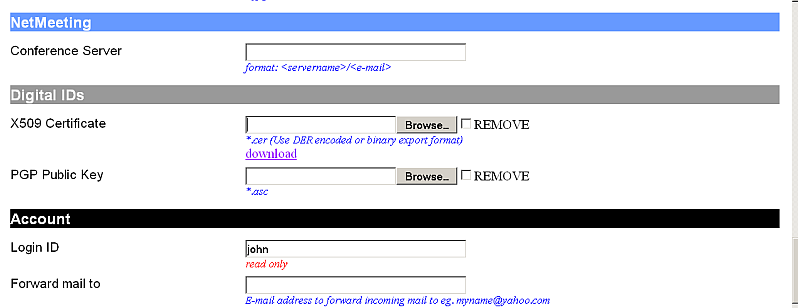
- The LDAP based WebId is ready to be used.
Verification Tests
- Make sure the steps from above are performed.
- If you generated Cert.
using ODS and enabled WebID login, attempt a WebID login:
- Access https://id.myopenlink.net/ods
- Select when prompted from your browser, the certificate generated from above.
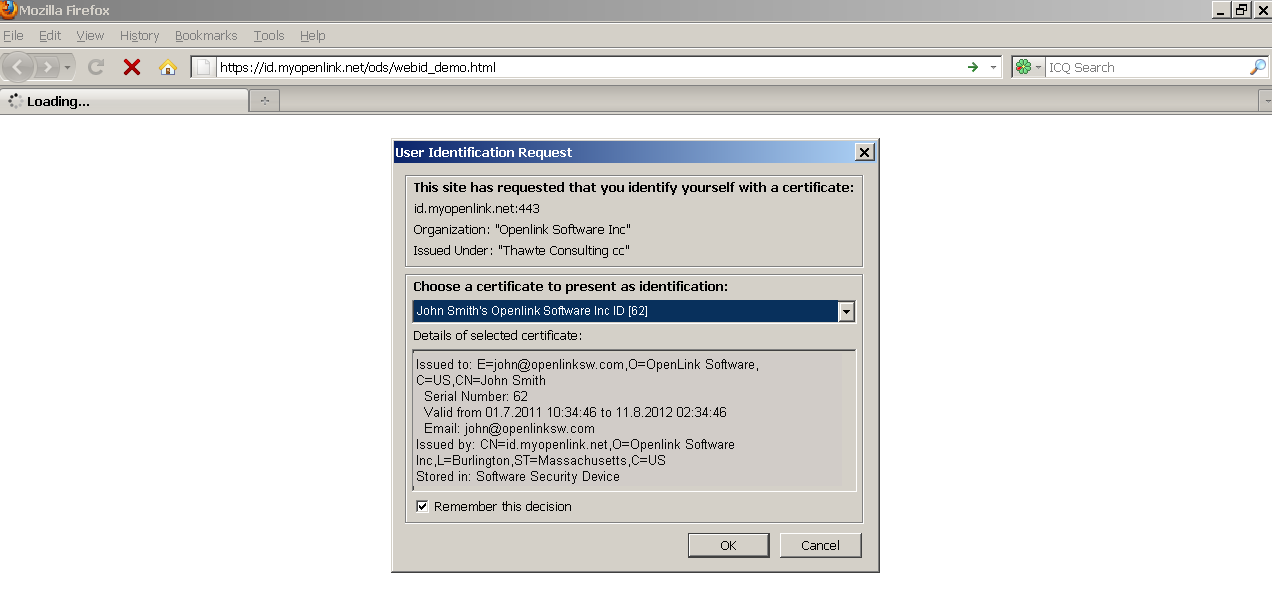
- As result should be presented the ODS Log in form.
Click the "WebID Login"
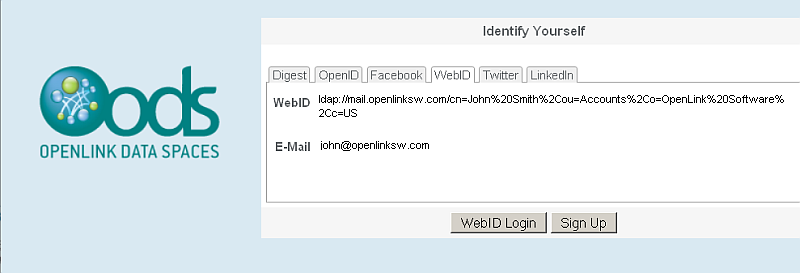
- Post successful authentication should show ODS home page for the logged in user
- Access https://id.myopenlink.net/ods/webid_demo.html

- Click "Check"
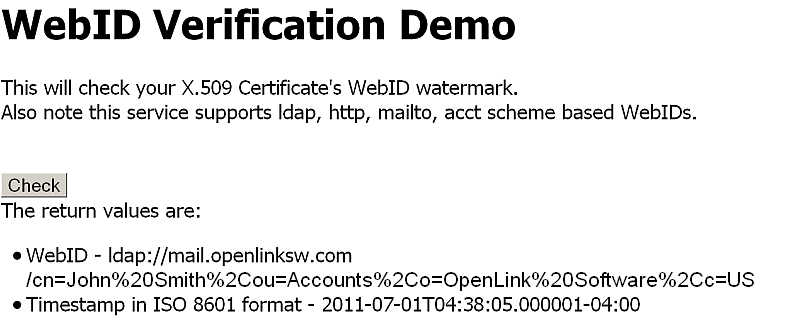
- The verification result message should be shown:
Other Examples
cURL Examples
Example with No Certificate using the WebID Testing Service endpoint at https://host/ods/webid_check.vsp $ curl -i -k https://localhost:4433/ods/webid_check.vsp?callback=http://localhost:8894/myapp/ HTTP/1.1 302 Found Server: Virtuoso/06.02.3129 (Win32) i686-generic-win-32 VDB Connection: Keep-Alive Content-Type: text/html; charset=ISO-8859-1 Date: Tue, 24 May 2011 11:15:09 GMT Accept-Ranges: bytes Location: http://localhost:8894/myapp/?error=noCert&ts=2011-05-24T13%3A15%3A09%2B02%3A00&signature=rT1gooyUcPjWo3yhIdx7y8j05oM%3 Content-Length: 0
Example with Valid WebID
$ openssl pkcs12 -in mykey.p12 > mykey2.pem $ curl -i -k --cert mykey2.pem https://localhost:4433/ods/webid_check.vsp?callback=http://localhost:8894/myapp/ Enter PEM pass phrase: HTTP/1.1 302 Found Server: Virtuoso/06.02.3129 (Linux) x86_64-generic-linux-glibc25-64 VDB Connection: Keep-Alive Content-Type: text/html; charset=UTF-8 Date: Tue, 24 May 2011 13:47:08 GMT Accept-Ranges: bytes Location: http://localhost:8894/myapp/?webid=http%3A%2F%2Flocalhost:8894%2Fdataspace%2Fperson%2Fdemo%23this&ts=201 00001-04%3A00&signature=7KYzL7vwpH2LtF4bZ%2FtAEWCC8gY%3D Content-Length: 0
Related
- Virtuoso Tips and Tricks Collection
- Power of WebID + OpenID Hybrid Protocol via Internet Explorer & Windows
- Using Safari to Demonstrate WebID + OpenID Hybrid Protocol Power!
- Using Virtuoso's WebID Verification Proxy Service with a WebID-bearing X.509 certificate
- Using Virtuoso's WebID Identity Provider (IdP) Proxy Service with an X.509 certificate
- WebID Protocol & SPARQL Endpoint ACLs Tutorial
- Safeguarding your Virtuoso-hosted SPARQL Endpoint
- SPARQL Endpoint Protection Methods Collection
- Virtuoso documentation
- Virtuoso Tips and Tricks Collection
- SPARUL over SPARQL using the http://cname:port/sparql-auth endpoint
- Virtuoso Authentication Server UI
- Manage a SPARQL-WebID based Endpoint
- Configure Virtuoso instance as an X.509 Certificate Authority and HTTPS listener
- Configure Virtuoso+ODS instance as an X.509 Certificate Authority and HTTPS listener
- WebID Protocol Support in OpenLink Data Spaces.
- Manage ODS Datadspaces Objects WebID Access Control Lists (ACLs):
- Guide for Set up a X.509 certificate issuer and HTTPS listener and generate ODS user certificates.
- Setting up PubSubHub in ODS
- PubSubHubBub Demo Client Example
- Feed subscription via PubSubHub protocol Example
- Setting Up PubSubHub to use WebID Protocol or IP based control lists
- CA Keys Import using Conductor
- Generate an X.509 Certificate hosted WebID Guide
- Generate an X.509 Certificate (with a WebID watermark) to be managed by host operating system keystore
- Generate an X.509 Certificate (with a WebID watermark) to be managed by a browser-based keystore
- ODS Briefcase WebID Protocol Share File Guide
- WebID Protocol Specification
- Test WebID Protocol Certificate page
- WebID Protocol Certificate Generation page
- openid4.me -- An early WebID+OpenID implementation that isn't currently functional, but still provides good insights into the inner workings of WebID+OpenID
- A nice OpenID service for testing the prowess of OpenID+WebID
- An WebID+OpenID protocol demo using ODS ...
- Using WebID from an iOS5 device (iPhone or iPad) with Twitter as the Identity Provider (IdP) service