Sponger Resource Allocation and WebID ACLS
What?
How to control user agent usage of sponger resources. In this case, HTTP connections to Linked Data transformation URLs.
Why?
More often than not, you would like to control access to your Sponger instance.
How?
Leverage the power of Vrtuoso's in-built WebID based ACLs which enables you apply basic and sophisticated rules that control user agent access.Sample INI setting
... [HTTPServer] ServerThreads = 100 MaxRestrictedThreads = 50 ...
This value sets an HTTP connection threshold for URLs consumed by user agents over http: . The remainder are exclusively accessible to user agents that present WebID watermarked X.509 certificates.
Simple Example
Prerequisites
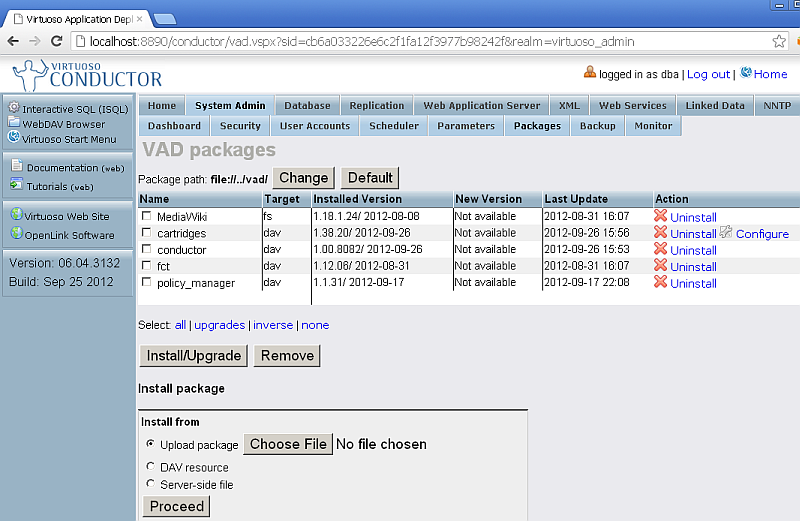
- Make sure the following packages are installed:
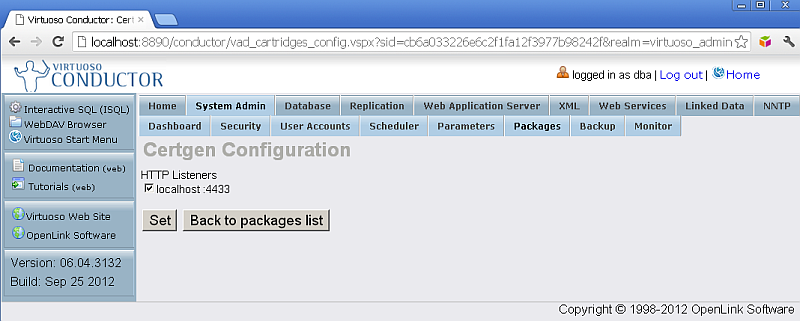
- Make sure Virtuoso HTTPS Listener is set up
- Make sure the
cartridgespackage is configured to use the HTTPS Listener from above:
Steps
- Assume a demo user with WebID:
http://id.myopenlink.net/dataspace/person/demo#this
- Generate X.509 certificate with WebID watermarks for the WebID from above ex.:
- Using Virtuoso X.509 Certificate Generator or
- Using the generator built into ODS. See more details here.
- Go to Conductor -> Linked Data Security -> Access Control:
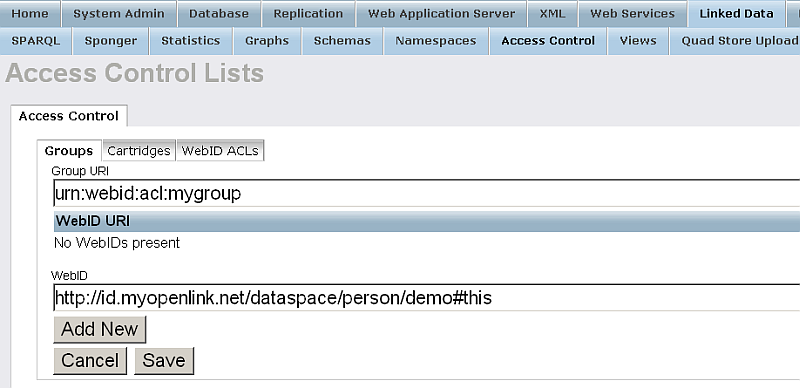
- Go to Groups:
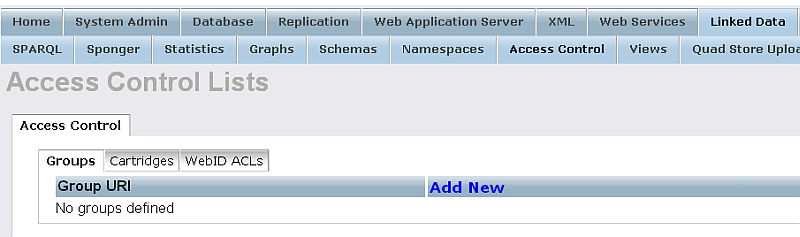
- Click "Add New":
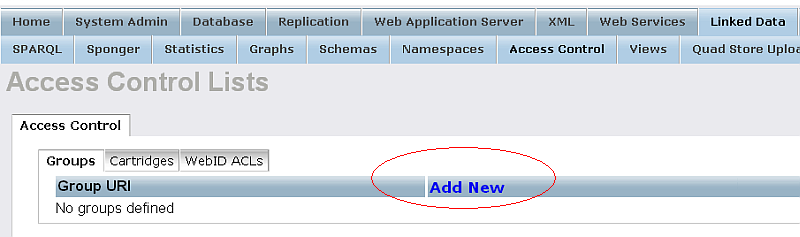
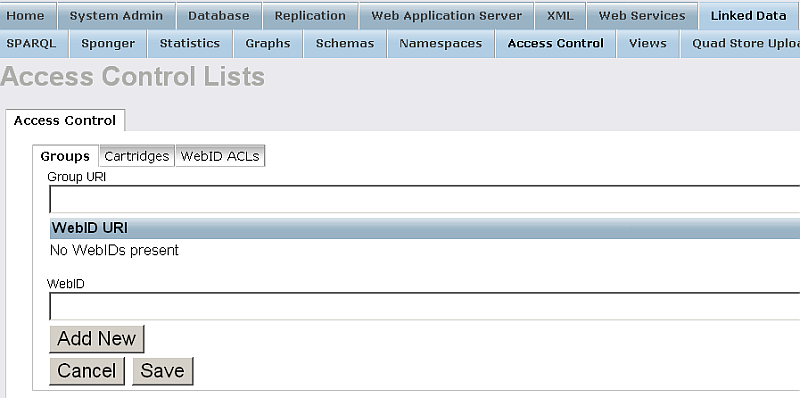
- Fill out the presented form with the following values respectively:
- Click "Add New" so to add the WebID to the Group WebID's List:
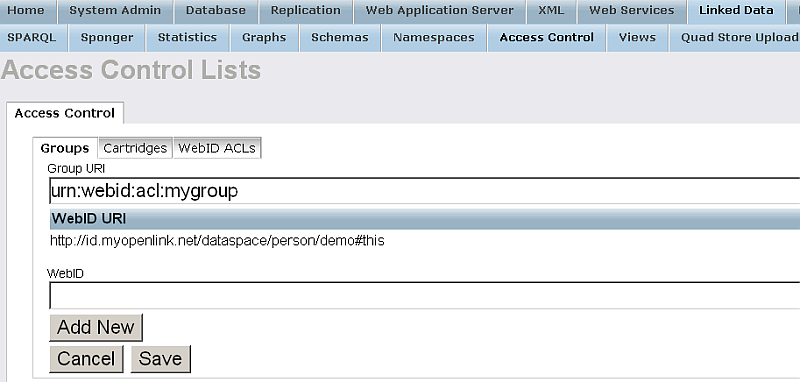
- You can add as many as you want new WebIDs following the steps from above.
- Finally click "Save"
- The WebID Group should be created:
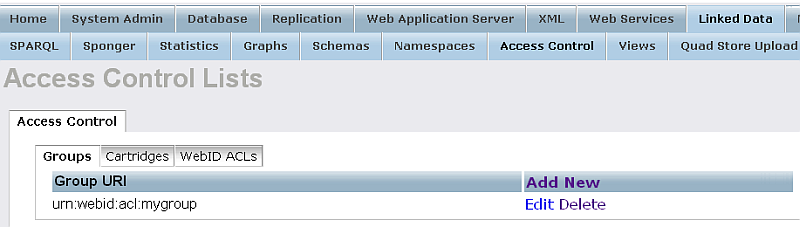
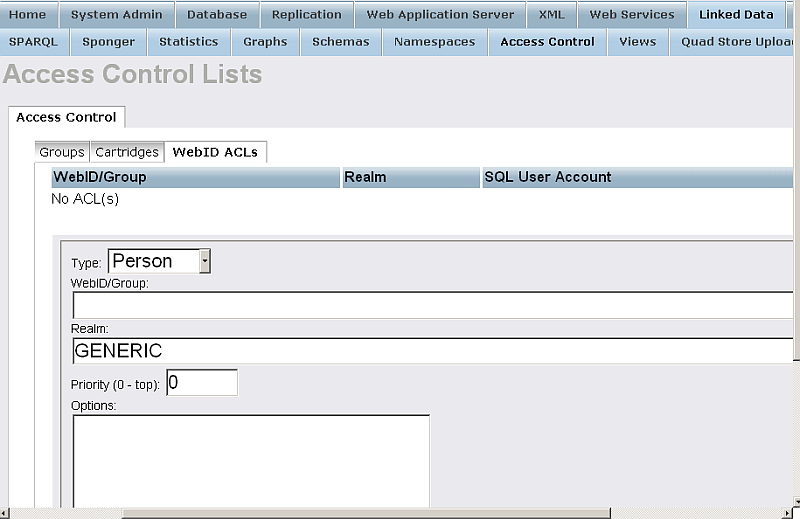
- Go to "WebID ACLs" tab:
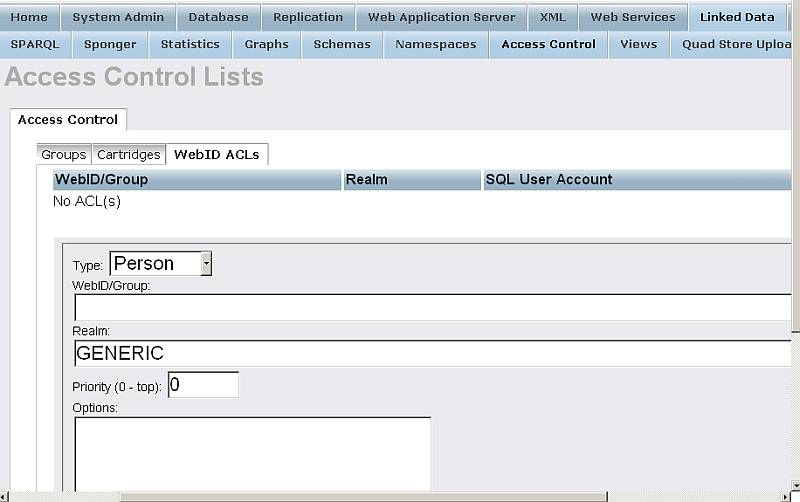
- Add WebID ACL associated with the group created from above:
- Change Type to "Group";
- Enter for WebID/Group the name of the group, i.e.: "urn:webid:acl:mygroup"
- Change Realm to "Virtuoso Sponger".
Note, the "Virtuoso Sponger" Realm name is obligatory to be entered exactly as "Virtuoso Sponger" to serve the needs of Virtuoso Sponger Resource Allocation with WebID ACLS:
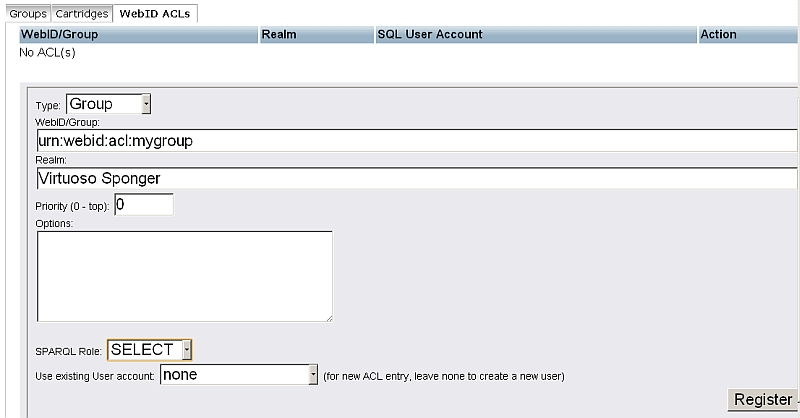
- Click "Register"
- The "WebID/Group" ACL should be created:
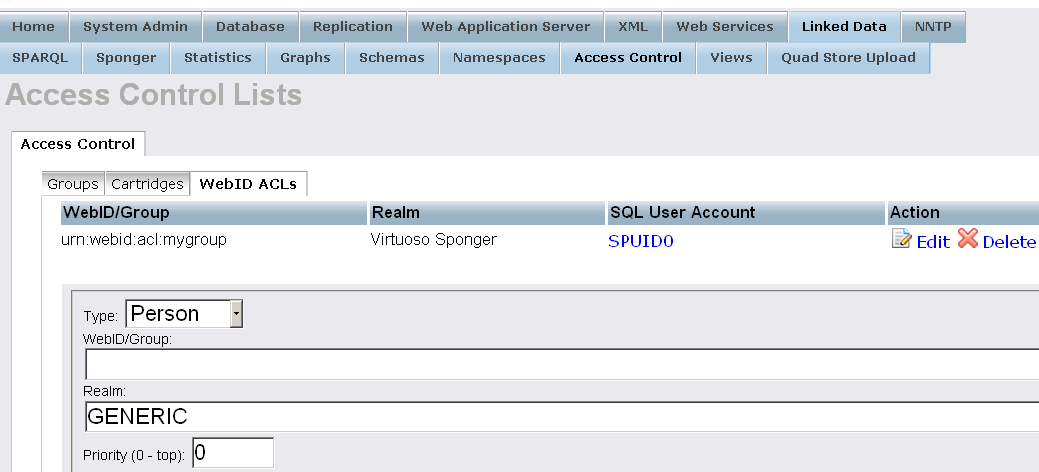
- Go to "Cartridges" tab and click "Add New":
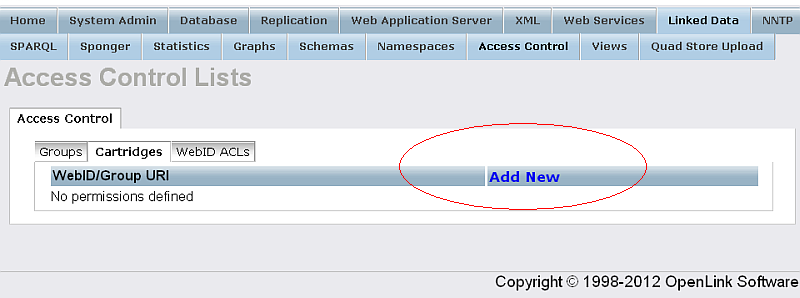
- Should be presented the list of all supported Virtuoso Cartridges:
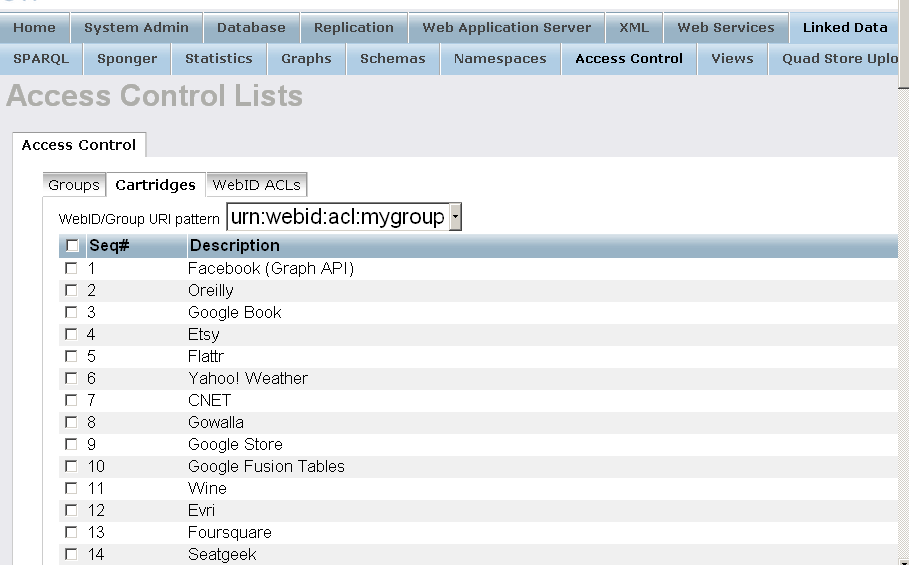
- Set for "WebID/Group URI pattern" the group created from above and select all cartridges:
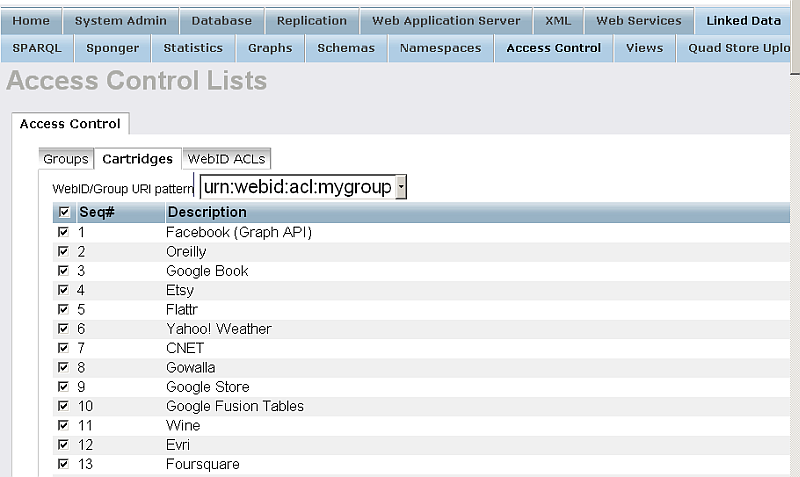
- Click "Save":
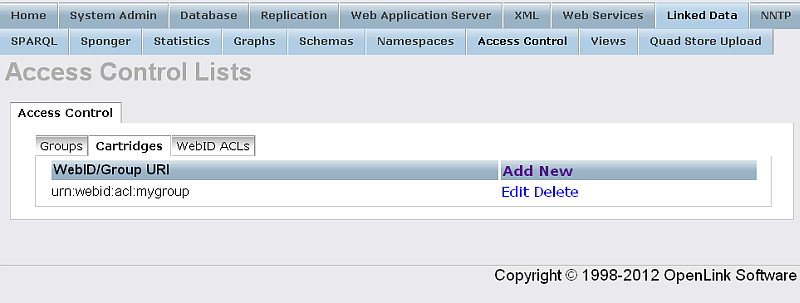
- The Cartridges WebId/GroupID URI is configured:
- Next we are going to sponge a url, for ex.:
http://google.com/ - Let's make sure there is no data locally in graph
http://google.com/:
SPARQL SELECT * FROM <http://google.com/> WHERE { ?s ?p ?o }; s p o VARCHAR VARCHAR VARCHAR ________________________________________________________ 0 Rows. -- 0 msec.
- Attempt to sponge our example URL i.e.
by accessing:
http://host:port/about/html/http://google.com/
- In this case there should be no retrieved data:
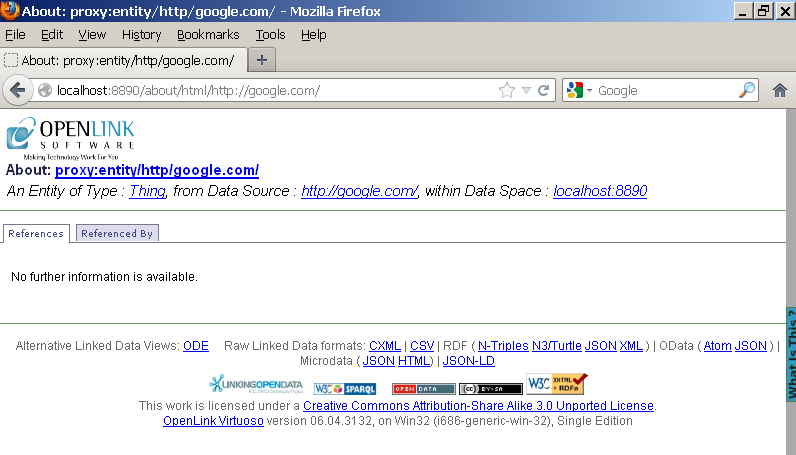
- Next perform sponge by accessing the following URL:
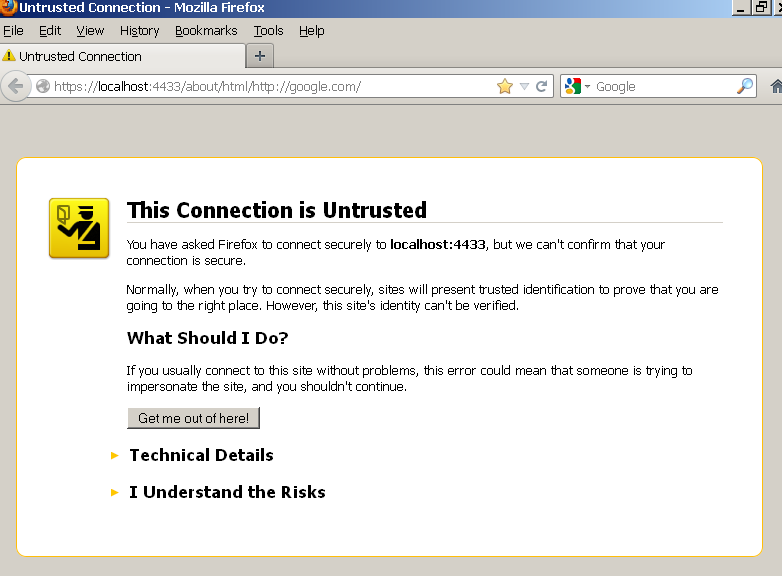
https://host:ssl-port/about/html/http://google.com/
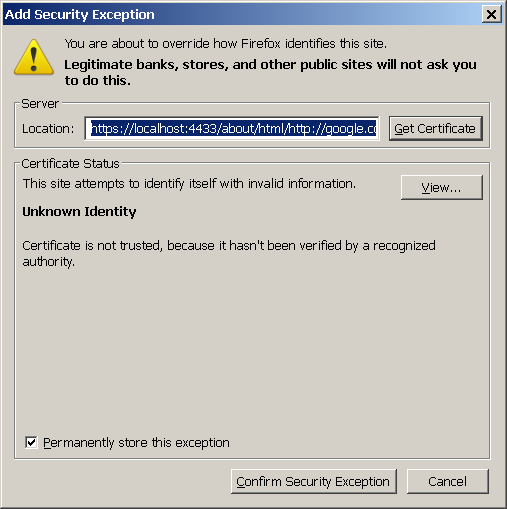
- Should be asked for certificate, choose the one generated from above:
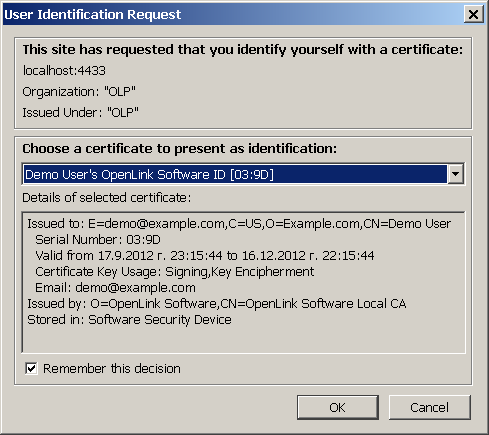
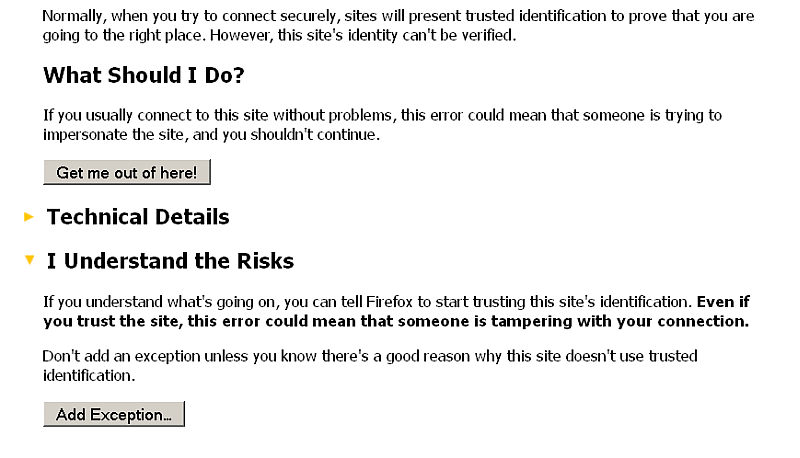
- In case of "This Connection is Untrusted" message is shown:
- The retrieved remote data should be shown:
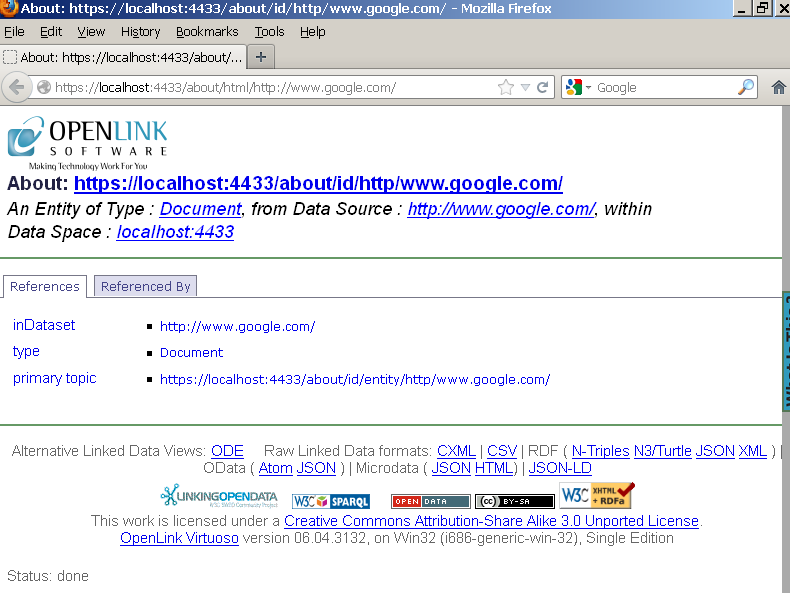
Related
- Virtuoso Tips and Tricks Collection
- Virtuoso Sponger
- Parametrized Examples of Meta Cartridge Usage via REST Request
- Meta Cartridges Usage via REST Request
- OpenLink-supplied Virtuoso Sponger Meta Cartridges
- OpenLink-supplied Virtuoso Sponger Cartridges
- Using Virtuoso's Delegated WebID Identity Provider Proxy Service
- Using Virtuoso's Delegated WebID Verification Service
- Generate an X.509 Certificate hosted WebID Guide
- Safeguarding your Virtuoso-hosted SPARQL Endpoint
- SPARQL Endpoint Protection Methods Collection
- Virtuoso documentation
- Virtuoso Tips and Tricks Collection
- SPARUL over SPARQL using the http://cname:port/sparql-auth endpoint
- Virtuoso Authentication Server UI
- Manage a SPARQL-WebID based Endpoint
- WebID Protocol Support in OpenLink Data Spaces.
- Guide for Set up a X.509 certificate issuer and HTTPS listener and generate ODS user certificates
- Configure Virtuoso+ODS instance as an X.509 Certificate Authority and HTTPS listener
- Configure Virtuoso instance as an X.509 Certificate Authority and HTTPS listener
- Setting up PubSubHub in ODS
- PubSubHubBub Demo Client Example
- Feed subscription via PubSubHub protocol Example
- Setting Up PubSubHub to use WebID Protocol or IP based control lists
- CA Keys Import using Conductor