Software Agent &
The OpenLink
The steps below outline how this can be done using the OpenLink
- Open the OpenLink
YouID certificate generation service ( http://id.myopenlink.net/youid/ ) in a Web Browser and login using one of the presented Single Sign on (SSO) services for Authentication (in this case we chose Facebook): 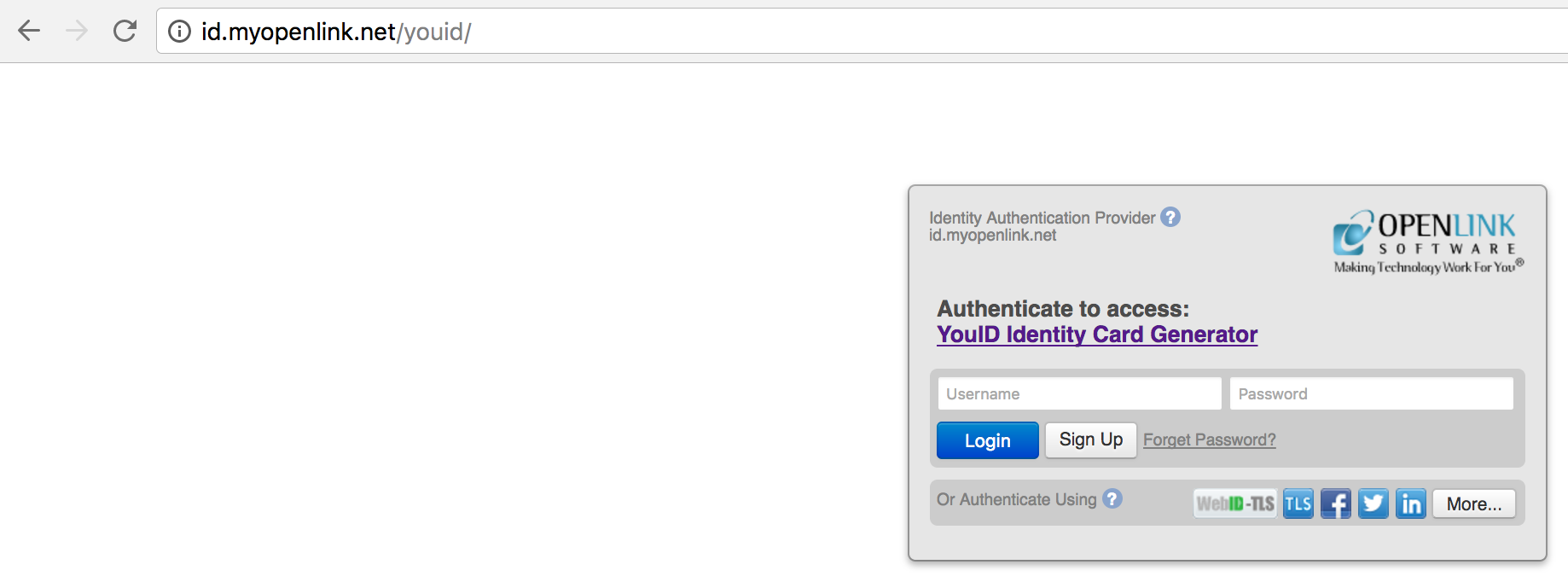
- Once authenticated click on the
Create New Identity Cardbutton to start the certificate generation process: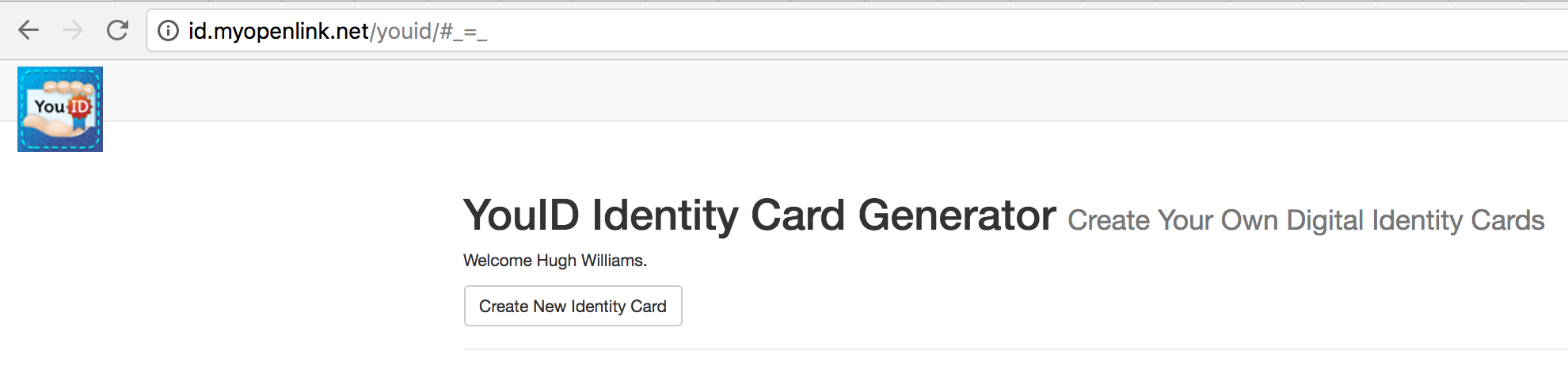
- The YouID? Identity Card Generator page is presented:
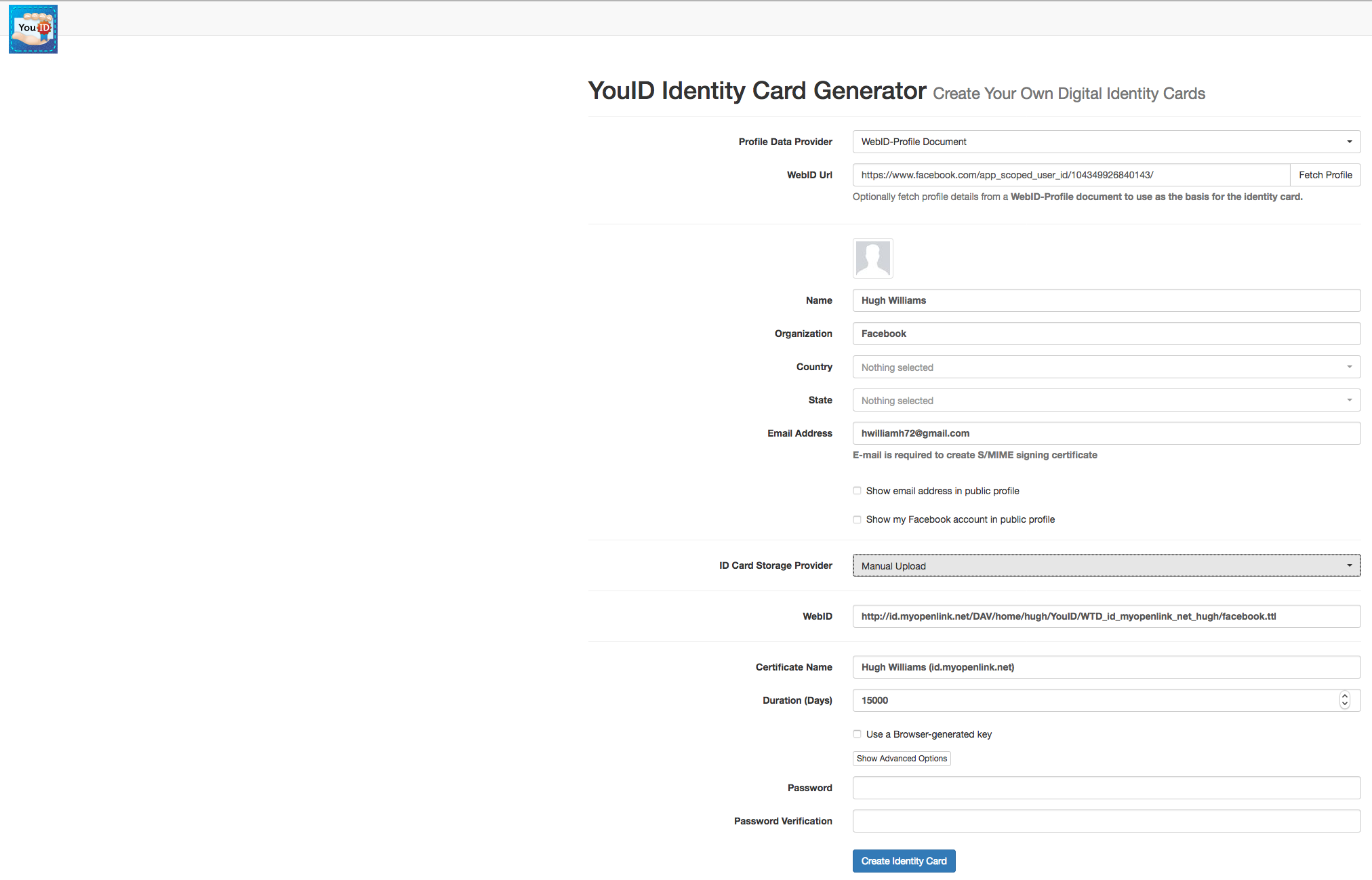
From which the following settings need to be made:
- Set the
Profile Data Provideroption toWebID-Profile Document - Set the
ID Card Storage Provideroption toManual Uploadfrom the top down list box - Set the
WebID - Set a
passwordfor the certificate
Click on the Create Identity Card button to generated the certificate.
4.
The Web Scale Verifiable Digital Identity Card is presented: 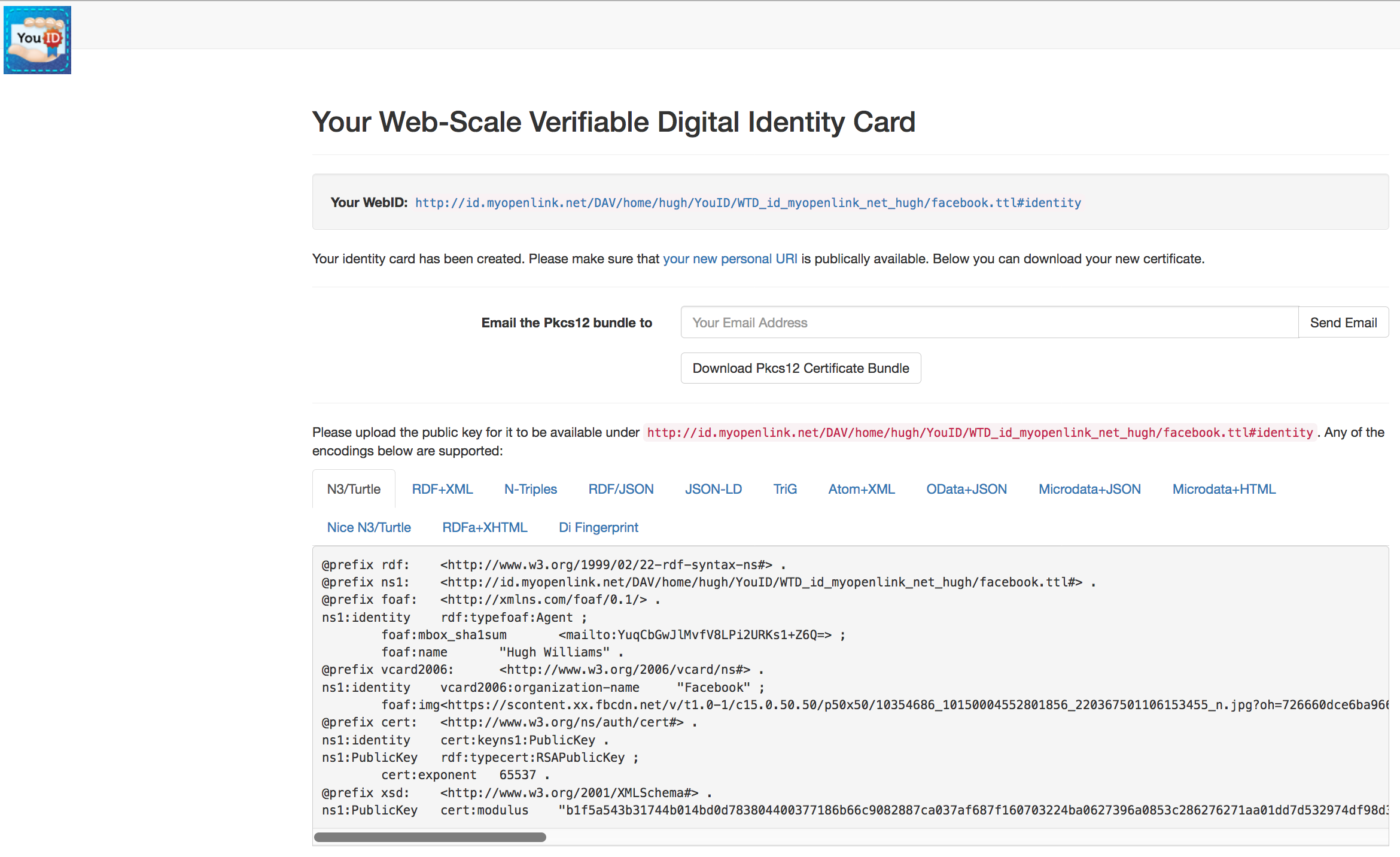
From where:
- The p12 public key can be downloaded for use when authenticating.
- The text of the generate public key in
N3/Turtleor any of the other supported formats should be copy and pasted to theWebID-Profile Document
5.
Add the following content to the end of the
## Profile Document combining credentials of Software Agent and Registered Users ##
## This document leverages the portability of relative hash-based HTTP URIs as Entity Identifiers ##
@prefix oplcert: <http://www.openlinksw.com/schemas/cert#> .
@prefix cert: <http://www.w3.org/ns/auth/cert#>.
@prefix acl: <http://www.w3.org/ns/auth/acl#> .
@prefix oplacl: <http://www.openlinksw.com/ontology/acl#> .
## Software Agent Credentials ##
<#identity>
foaf:name "A Software Agent" ;
oplcert:onBehalfOf <#wtd> ;
cert:key [
cert:exponent "65537"^^xsd:integer ;
cert:modulus
"b1f5a543b31744b014bd0d783804400377186b66c9082887ca037af687f160703224ba0627396a0853c286276271aa01dd7d532974df98d307797775c590955cc9c8993bdf6429462a9cc763bb74593c69463a2b8729a80ed17c18a5a766fada055eb69bbd5dc31a4b14c6f154d152c2d7ae83f66f0e61ee82ae85838f501eef5eabd1a4b031d612a4a6a5d6f9e4f53480c405ff51838e9cfcbf4c80a1ac9628c9e18b22a3cd4457b090e186845d6243160d151a3b2c02792312c70d620a954498913fde9ffcb09abb1cd2ad0ba28fa384b6b36255fd7b9b3be55cb31897c88f00eb3a24aaff2c8587f01d0fd5a399aa6b4b5486b6c38275cb08391662b3ba7f"^^xsd:hexBinary
] .
## User Credentials (OnBehalfOf relation participants) ##
<#wtd>
oplacl:hasIdentityDelegate <#identity> .
Key Points
In the
- It is being used as both the application software agent's and delegating users' shared profile document.
If it is preferred to have separate delegating user profile documents, this can be done - the URL of each user's distinct profile document is simply pointed to by the
oplcert:onBehalfOfproperty in the software agent's profile document, similar to the shared profile document example above. But there is a strong case for a single document being used for ease of management. - The
oplcert:onBehalfOfattribute is used to reference theWebIDs (each contained within a user profile document) of the users the software agent is authenticating on behalf of. - The
oplacl:hasIdentityDelegateattribute identifies theWebID of the software agent that acts as a delegate of connecting users, authenticating on their behalf. As indicated, the user WebIDs can be stored in separate user WebID profile document if preferred. - The
cert:keyattribute contains the public key of the software agent certificate, which is actually included (but not shown here) in itsYouID auto-generated profile document i.e. profile.ttl and thus can be seen from the generated content. Particularly if separate software agent and user profile documents are used (but still required if a combined document is used), inclusion of the software agent's public key in the user profile document provides a critical validation check between the software agent and the delegating user who is authorising the OnBehalfOf connection. - Only one public key is required.
Irrespective of whether a single or separate profile documents are used, it/they contain just the public key of the software agent.
When using
WebID authentication delegation, the users being authenticated do not require a public/private key pair. They require only a WebID - this can be provided without needing TLS, for instance by one of many third-party OAuth-based authentication services supported by VAL, and hence without needing a user key pair, so reducing the administration overhead when authenticating many users.